Cyber Warfare
3 min read
What is Cyber Warfare
Cyber Warfare is generally a politically motivated attack through the use of technology and cyberspace. These attacks involve different virus' and malicious software that are clandestinely sent out in order to hack into a specific database or server. These attacks can result in physical destruction or loss of life which then can be considered acts of terrorism.
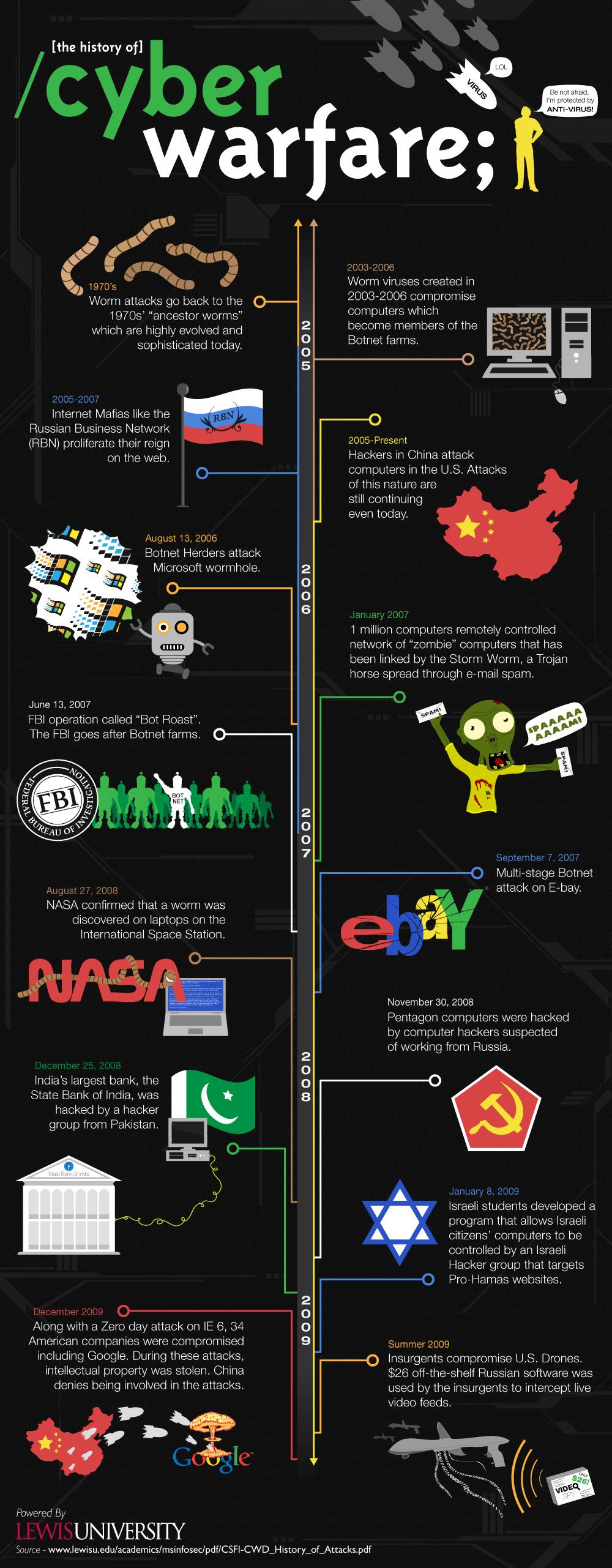
Origin of Cyber Warfare
As simple virus' and worms have been around since the 70's and cyber attacks were not much more than identity theft and money scamming until 2008 when there was a worm found on the laptops in the international space station which later lead to a virus in the Pentagon, rumored to be from the russians. Since then financial institutions were hit next in 2008 after the first bank, The State Bank of India (india's largest bank), was attacked by hackers in pakistan which lead to a forced shutdown of the bank until the issues were resolved
How are Cyber Hacks Conducted
- People can search through codes to find mistakes and ways to get around securities in the system
- Phishing links are used to extract personal information using fake emails or links that the victim would click thinking its real
- DDos (Distributed Denial Of Service) is where a large amount of traffic is sent to a system to crash it making it no longer available for general public
Threat Levels of Cyber Warfare
There are three elements of cyber warfare: Sabotage(identity theft), electronic espionage(cyber theft/malware), and attacks on power grids which are the most alarming.
Sabotage would be something along the lines of Taking down a service so a business is no longer making money or stealing someones identity. Identity theft is something that happens every day
Electronic espionage is when someone tries to hack into a database to steal files and information that they should not be allowed access to in the first place. i.e. The russians involvement in the political campaigns of 2016 as well as china stealing blue prints while under a cyber war truce
What Happens in the Real World
The chinese have been known to hack into the DOD to steal blueprints for fighter jets.
According to CNBC "Despite a cyber-warfare truce, one defense analyst said China is probably still engaged in the theft of sensitive U.S. military technology."(Daniels)

Countries will often try to get in the middle of other countries elections through hacking to levy it to a certain side for their own personal gain. Even though no evidence has been found that the russians have been involved with messing with the 2016 election it is to be believed that they did play some role with the image the public saw of the democratic candidates.
Why is Cyber Warfare Viable
Real war is a battle of attrition in which the winning side tends to be the side with greater resources. This is not the case with cyber warfare. Very little resources are needed and malicious software can be made by pretty much anyone with a computer. It does not take much to do a lot of damage. Also unlike real war were it could take millions of people to accomplish something in cyber warfare it could just be one person behind it all.
Sources
- https://content.sentrian.com.au/blog/a-short-history-of-computer-viruses
- https://securityaffairs.co/wordpress/6776/security/the-cyber-war-era-began-long-ago.html
- https://www.cnbc.com/2017/11/08/chinese-theft-of-sensitive-us-military-technology-still-huge-problem.html
- https://www.equifax.co.uk/resources/identity_protection/how-cyber-attacks-happen.html