Historic Cybercrime

5 min read
What is Cybercrime
According to Michael Aaron Dennis for Encyclopedia Britannica, Cybercrime is the utilization of a computer in order to commit certain online crimes like committing fraud, trafficking in child pornography and intellectual property, stealing identities, violating the privacy, and many more.
The development of technology and specifically computers resulted in a whole new branch of crime that is cybercrime. A majority of cybercrimes are some sort of seizing of information, whether that be from the government, personal, or from a business.

Most Common Types of Cybercrimes
- Hacking - involves partial or complete acquisition of certain functions, networks, or websites.
- Identity Theft - Form of fraud where personal data is stolen
- Fraud - General term for cybercrime intended to deceive people for important data or information
- Scamming - Forcing users to pay for computer repair, troubleshooting, IT support for problems that may not even exist
- Computer Viruses - Gains unauthorized access to steal important information and data
- Ransomware - Encrypts files and information through public-key encryption
- Distributed Denial of Service Attack - This is a distraction which prevents the computer from functioning normally making it easier to hack into
- Botnets - Controlled by remote attackers, usually work on businesses and government in because they target the information technology infrastructure
- Spamming - Electronic message systems with fake links, malware, and other malicious programs
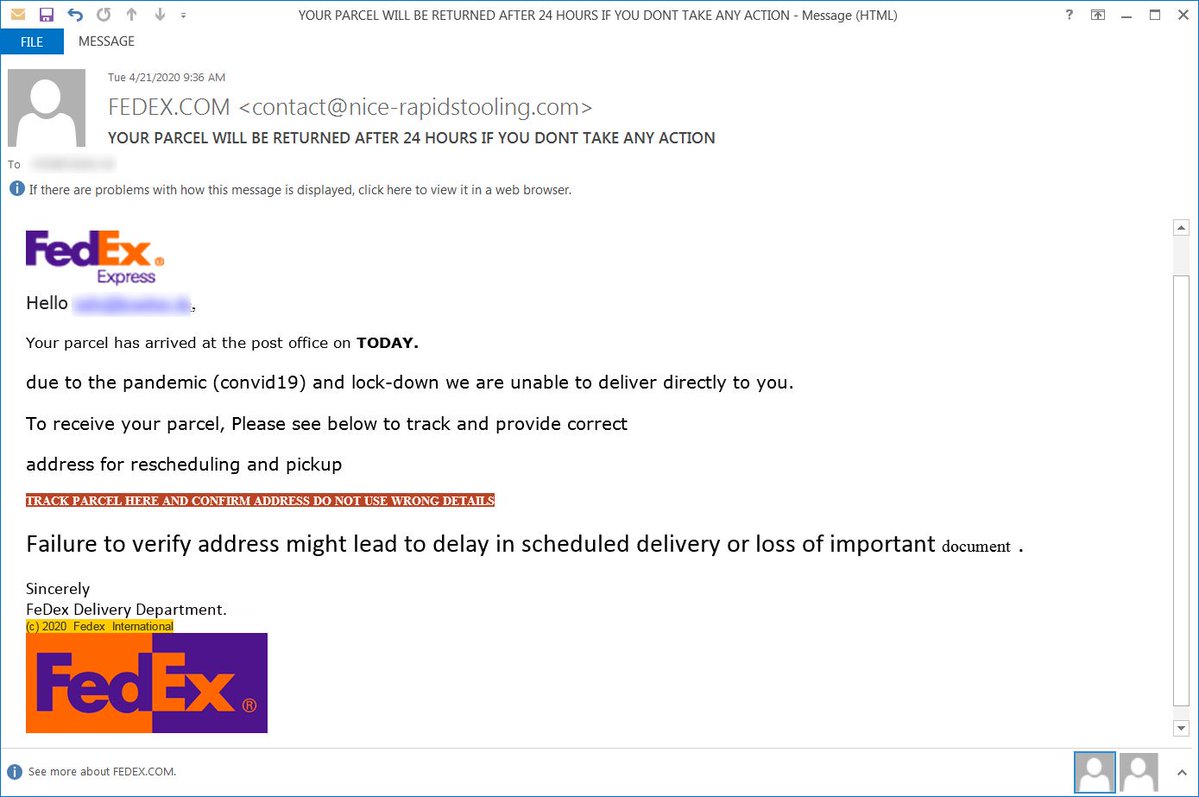
- Phishing - Pretend to be company and organization in order to steal confidential information
- Social Engineering - Make direct contact with people to try and steal their information
- Malvertising - Filling websites with advertisements and malicious codes
- Cyberstalking - Following a person online anonymously
- Software Piracy - illegally duplicating original content and posting it on the internet
- Child Pornography - Pornography depicting children posted online
- Cyberbullying - Online bullying carried over the internet
Morris Worm Cyber Attack (1988)
The Morris Worm cyber attack was the first major cyber attack. Occurring at 8:30 p.m. on November 2, 1988, a program was released from a computer at MIT. The worm soon affected 10 % of all 60,000 functional computers online within one day. The attack crippled the functions of top institutions and the military. The loss of production and ensuing attempts to remove the worm cost upwards of $100,000 and has even been projected to have cost millions.
After an anonymous tip, the perpetrator was revealed by The New York Times to be Robert Tappan Morris, a 23-year-old Cornell University graduate student. Despite claiming it to be an accident, the FBI was able to procure evidence establishing intent. Morris was convicted under the 1986 Computer Fraud and Abuse Act. Morris became the first individual to be convicted under the act and was subsequently sentenced by a jury to community service, a fine, and probation. This attack served as an alert to the liabilities in the online network infrastructure and showed the effect that an attack can have on our society.
DDoS Internet Attack (2002)
The internet was hit directly, marking a first in the history of cyberattacks. By targeting the thirteen Domain Name System (DNS) root servers, a DDoS attack assaulted the entire internet for an hour. While most users were unaffected, the DDoS attack could have shut down the internet if it had been sustained for a longer period. Up until this point, there had never been such a sophisticated cyber-attack launched on such a large scale.
In the beginning, the attack hit seven servers that were on the top of the domain name system and they were all rendered inaccessible. However, within that one hour of the cyberattack, all of the thirteen servers were affected. This attack was most likely done overseas, which controlled the hundreds of drones that flooded the servers with internet traffic.
After one hour of damage, the servers were rebooted and brought back online for public use ending the virtual attack. This was the first attack of its kind in size and method which led to increased security for servers.
NASA Breach (2002)
One of the largest attacks on NASA ever occurred in 2002 when 15-year-old Jonathan James was able to hack into some NASA computers and create a backdoor method that allowed him to re-enter into the software. This backdoor enabled him to intercept thousands of highly secretive emails from a pentagon computer, as well as learn new passwords so he could access other information as well. With the information he acquired, James was able to steal a piece of NASA software that protected the International Space Station.
The 15 year old James ended up pleading guilty to juvenile delinquency and spent 6 months in jail. To this day it is one of the largest breaches of information ever from NASA, and it was done by a 15 year old.
How to protect yourself from cyber crimes
Norton, a popular digital security firm, recommends using software to protect yourself on the internet from malware and to make sure you protect important private and financial information when you’re online. Other ways you can protect yourself from cyber crimes are to use complicated passwords, making sure important files aren’t stored on the internet, and not responding to texts, emails, or pop-ups that ask for your personal information or login information.
Other ways you can protect yourself are not opening links in email that don’t look legitimate and not opening attachments. These links and attachments are often described as safe things, but often, they lead to opportunities for hackers to get access to information on your computer.
Sources
- https://www.voipshield.com/the-16-most-common-types-of-cybercrime-acts/
- https://us.norton.com/internetsecurity-how-to-how-to-recognize-and-protect-yourself-from-cybercrime.html
- https://www.britannica.com/topic/cybercrime
- https://www.investopedia.com/financial-edge/0712/6-ways-to-protect-yourself-against-cybercrime.aspx
- https://www.fbi.gov/history/famous-cases/morris-worm
- https://gomindsight.com/insights/blog/history-of-cyber-attacks-2018/
- https://www.theregister.co.uk/2002/10/23/feds_investigating_largest_ever_internet/
- https://www.arnnet.com.au/slideshow/341113/top-10-most-notorious-cyber-attacks-history/
- https://abcnews.go.com/Technology/story?id=119423&page=1