Identity Theft

5 min read
WHAT IS IDENTITY THEFT
Identity theft is an extremely common form of cybercrime in the United States. According to the Federal Trade Commission, around nine million Americans experience identity theft yearly. However, what exactly does it mean to have your identity stolen, and how do criminals do it? It's natural to think of our identity as people the attribute that's make up a person - what someone looks like, their race, their values, what makes them laugh, etc. However, this is not the Nicholas Cage and John Travolta movie Face Off, the criminals don’t physically take what you presume to be your personal Identity. Rather, according to the Federal Trade Commission, identity theft occurs when someone achieves access to another person's Social Security number, credit cards, debit cards, or other specific personal information, and in turn uses those things to open new accounts, make purchases, or get a tax refund. Essentially, the criminal steals financial and governmental information from another person.
HOW DOES IDENTITY THEFT OCCUR
Identity theft is extremely common because of how easy it is to do. There are multiple different types of identity theft each requiring different methods of crime
These are the types of Identity Theft involving technology:
Skimming: This occurs when a person uses their credit/debit card and the reader device collects information from the magnetic strip on the back of the card. Prevention: Check bank statements frequently and use cash more often
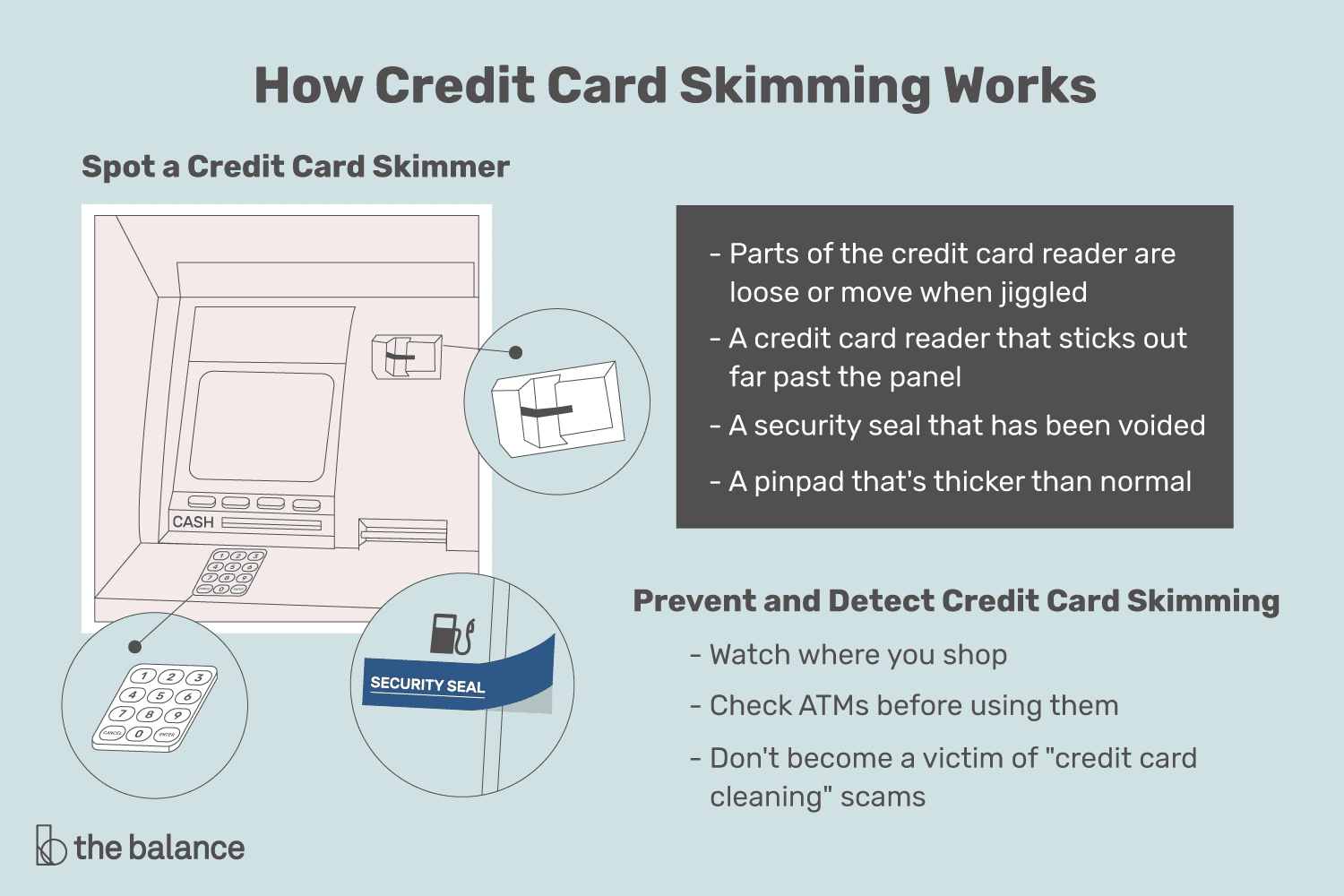
Pretexting: This occurs when a scammer contacts the victim under a false pretext urging the victim to give them personal information like their SSN, credit/debit card number, bank routing number, answers to security questions, etc. The criminal will create a new identity often posing as a company or person that the victim would trust by calling the victim and asking certain questions. Prevention: VERIFY YOUR SOURCE! This is the number one way of preventing fraud from happening to you. Always, always, always check to make sure the email or phone number is directly associated with the person or company before giving any personal information.

Phishing Schemes: The Federal Trade Commission defines Phishing scams as "Scammers use email or text messages to trick you into giving them your personal information. They may try to steal your passwords, account numbers, or Social Security numbers. If they get that information, they could gain access to your email, bank, or other accounts. Scammers launch thousands of phishing attacks like these every day — and they’re often successful".
- These emails often come from someone you would trust
- It often disguises itself as a link to infiltrate ones technological software
How to Identify potential Phishing Scams
The FTC gives a list of common messages scammers will use to get someone to click a link:
"Phishing emails and text messages often tell a story to trick you into clicking on a link or opening an attachment. They may…"
- say they’ve noticed some suspicious activity or log-in attempts
- claim there’s a problem with your account or your payment information
- say you must confirm some personal information
- include a fake invoice
- want you to click on a link to make a payment
- say you’re eligible to register for a government refund
- offer a coupon for free stuff
Here's an example of a phishing email:
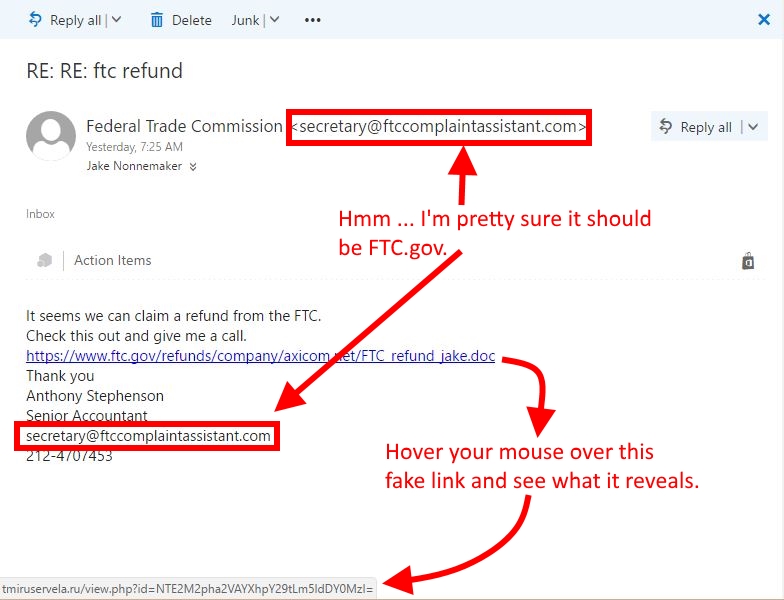
Prevention:
- Download software security
- Download ad blockers
- Verify the source of the email before clicking any links
- Never give away the answers to your security questions
- Frequently back up your data
Signs that You might be a victim of Identity theft
- Unfamiliar charges on your debit or credit card
- Emails from unfamiliar websites using your information
- You get a notice from the IRS
- Your bank provider notices a change in typical behavior around purchases, loans, tax refunds. Etc.
- Specific have your information without your previous knowledge

What to do If you’re a victim of Identity theft
The FTC has a specific website where people who suspect criminal activity can go to report identity theft: https://www.identitytheft.gov
They also suggest that you..
- Call the companies where you know fraud occurred.
- Place a fraud alert on your credit reports and get copies of your report.
- Report identity theft to the FTC.
- File a report with your local police department"
Sources
- "Carson City." Identity Theft | Carson City, www.carson.org/government/departments-g-z/sheriff-s-office/about-us/divisions/investigations/identity-theft.
- "How to Recognize and Avoid Phishing Scams." Consumer Information, 24 Mar. 2020, www.consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams.
- "Identity Theft." Consumer Information, 17 May 2019, www.consumer.ftc.gov/articles/0005-identity-theft#signs.
- Irby, LaToya. "What Every Consumer Needs to Know About Credit Card Skimming." The Balance, The Balance, 5 Feb. 2020, www.thebalance.com/how-credit-card-skimming-works-960773.
- Most Common Schemes - Identity Crimes - Center for Identity Management and Information Protection (CIMIP) - Utica College, www.utica.edu/academic/institutes/cimip/idcrimes/schemes.cfm.
- Nonnemaker, Jake. "Your Computer Belongs to Us Now - Anatomy of a Phishing Scam - Part 2 - Westlake Village, Agoura Hills, Thousand Oaks, Conejo Valley, San Fernando Valley." Axicom, 27 Apr. 2017, www.axicom.net/2017/04/computer-belongs-us-now-anatomy-phishing-scam-part-2/.
- "Substantial Support from State Attorneys General on Identity Theft Rules." Corporate Compliance Insights, 8 Apr. 2019, www.corporatecomplianceinsights.com/substantial-support-from-state-attorneys-general-on-identity-theft-rules/.
- White, Martha C. "Here's How Your Identity Will Be Stolen: The Top 10 Scams."
- Time, Time, 5 Apr. 2012, business.time.com/2012/04/17/10-ways-youre-going-to-get-your-identity-stolen/slide/2-pretexting/.