Navigating Suspicious Websites

9 min read
What Constitutes a Suspicious Website
A suspicious website is any type of unsecured or otherwise dangerous page on the Internet that attempts to virtually invade your privacy. These types of sites are often referred to as phishing or malicious websites and will present themselves as honest websites. The functions of a suspicious website can include disrupting computer operations, gathering personal information, downloading unwanted programs, and even gaining total access to your computer. Although these websites can be very harmful to your computer, there are always appropriate precautions to take to prevent your computer from being threatened or infected with malware and viruses.
How Do I Know If a Website is Suspicious
Ultimately, it is the users themselves that have to decide whether or not a website is legitimate. There are a few key things to look for to keep your computer protected and browse the internet safely:
Check the URL
Simply misspelling the URL of a website you wish to browse puts you at risk of going to a potentially malicious website instead. Hackers will often create websites that imitate real companies with one or two letters changed in the URL in hopes of gaining access to your information. Make sure the spelling, punctuation, and jumbles of characters at the end of website URLs are in the correct order. If you encounter a hyperlink, be sure to hover over the text to reveal the destination of your potential click. In addition, websites may use similar design and content in order to further trick the user into clicking something on the website, which may steal information, otherwise known as phishing.
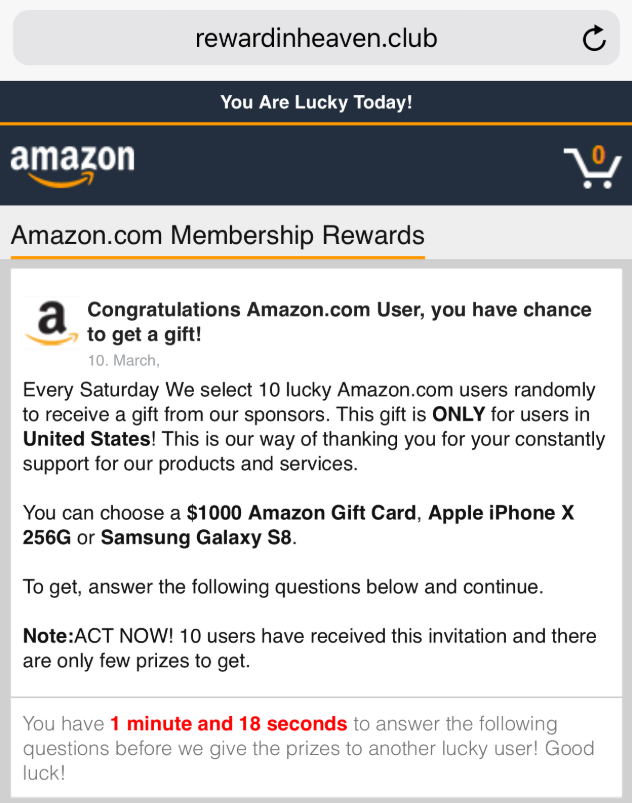
On this site, a similar design of "Amazon.com" is used, including the logo. However, the URL address clearly conveys that it is not the correct website.
Analyze the Layout/Design
The format and design of the site can also give away the illegitimacy of a website. Depending on the scale and reputation of certain companies and organizations, there has to be a degree of professionalism and organization upon first glance of the layout on their website. This especially holds true for larger corporations and institutions. Never trust an undeveloped, sketchy-looking website. This can include spelling and grammar errors, sentences that don’t make sense, or low-resolution, grainy logos. Be aware, however; scammers could potentially make sites that look attractive and legitimate but are still malicious.
Avoid Attempted and Unwanted Downloads
Aggressive pop-ups after first opening the link are never a good sign. Suspicious websites will often ask you to download an "update for your outdated Flash Player" or inform you that "your computer has been infected by spyware" in these pop-up tabs. Immediately close any windows in relation to the website, as these methods of downloading unwanted programs onto your computer. Additionally, if there are any wanted downloads, make sure that the file format such as .exe or .dmg is correct and corresponding to your device.
Check for SSL Certification
The most important, and least obvious, the key to a safe website is the proof of an SSL Certificate. An SSL or Secure Sockets Layer Certificate is a global standard of website protection that encrypts the secure data within the website. Things to confirm a website has its SSL Certificate include the use of HTTPS in the URL instead of HTTP in addition to a padlock symbol next to the URL in the browser. According to Google, HTTPS encryption on the web, as of April 25, 2020, has reached an all-time high at 95% of websites across their platform. You should avoid banking and/or entering your credentials on sites that do not have a secure connection or the "https" keyword before the URL of the site.
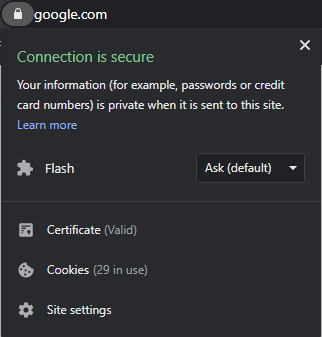
In common browsers, there are typically indicators to show whether the connection to a website is secure and if the SSL certificate is valid. On this browser, it is shown on the left of the address bar when clicking the padlock symbol.
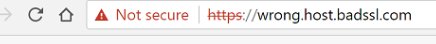
However, this is an instance where your browser shows that your connection is not secure, and hackers may be trying to steal your information.
How Can I Navigate the Suspicious Website
Advertisements
Although some ads are genuine, other times, ads may show up in the form of adware. These ads are more malicious, and oftentimes are either "clickbait", or try to disguise themselves as relevant content in order for the user to click on them. Websites may also show you popups or open pages that have misleading information.

Common "clickbait" ads feature headlines that tempt the user into clicking them. This content may be malicious in nature.
Adware can do things such as: collecting information like location and personal browsing history, forcefully redirecting your browser to another website, displaying pop-ups, and downloading unwanted files.
Getting Rid of Ads
Most well-known browsers have the option of using extensions, which allow you to customize your internet user experience. Extensions such as advertisement blockers have become very popular, as they do a very efficient job in blocking all unwanted advertisements. Some public school systems, such as Montgomery County Public Schools in Maryland, have installed extensions such as "uBlock Origin" on school laptops to keep students away from malicious content, advertisements, and popups.
uBlock Origin is an open-source software widely used today to block advertisements.

Website Links/Hyperlinks
If you are suspicious of a link, you can hover over it to see where it leads. Sometimes, this might not give you the right information, since the creators of the website could put Japanese characters or other unusual Unicode symbols in the URL that look like punctuation, but are not, in fact, according to https://www.spamtitan.com/web-filtering/critical-security-vulnerabilities-in-browser-plugins-addressed/. The way this can cause problems is when malicious actors create URLs with unusual characters that look like, for example, a forward slash. Doing this creates URLs which look perfectly valid and like another site, but are actually something completely different. An example could be www.google.comノ (the last symbol is not a slash!)
As well as this, some hyperlinks may disguise their destination using URL shortening services. A bit about those: URL shorteners simply create a URL that links to their domain, which they then redirect to some other site that has been assigned to the shortened URL. Common URL shorteners include Bit.ly and adf.ly. Note that sometimes you may still know where the shortened URL goes, because a URL shortener may have special formats for especially popular websites; for example, Bit.ly shows shortened links to Amazon webpages as "amzn.to" followed by the rest of the URL.
If you are comfortable using somewhat advanced features of your browser, you can try using "developer" or "debug" mode to investigate the properties of a hyperlink or other web page element, to determine whether it will try to open a new tab, or initiate a download, etc.
How to Get What You Are Looking for
If you’re trying to download something from a website that you are suspicious of, you should take care to make sure that you are clicking on the correct download links. If there are many indistinguishable download buttons, it may be better to find whatever you are looking for at a different site. Watch out for buttons that look like grainy pictures, or buttons that are on the margins of the pages. It is also good to avoid buttons that look like they are parts of advertisements. Installing an advertisement blocker may help with this.
What Should I Do After I’ve Visited the Suspicious Website
After Downloading
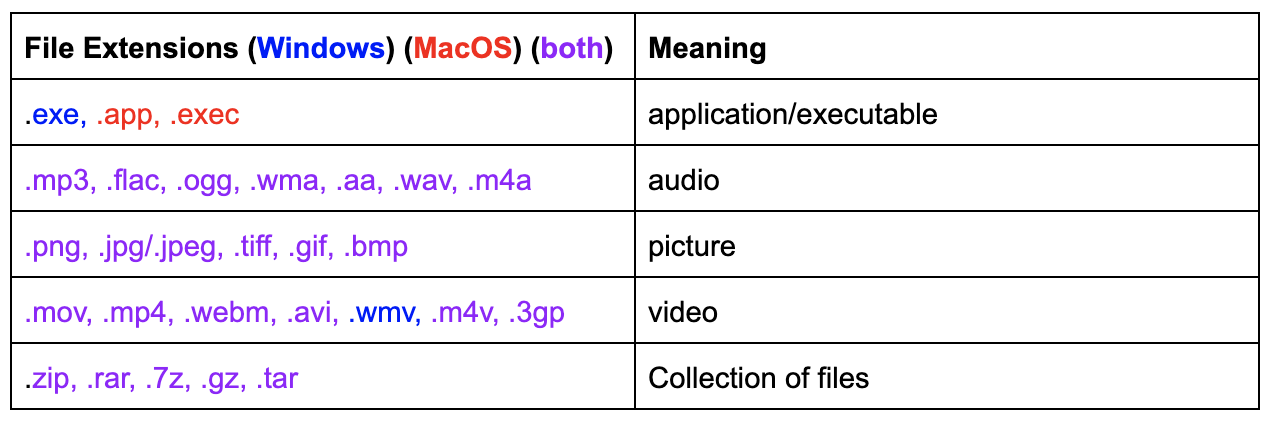
One of the most important steps, after you’ve downloaded something from a suspicious website (that you wanted to download in the first place), is to verify that it is the correct file type. For example, if you downloaded music, you should check that the file is an audio format, and if you downloaded a video, for example, you should check that the file is in a video format. One thing to watch out for especially is if you did not attempt to download a software application is your downloaded file is a .exe type (on Windows). Following is a chart of different file extensions and what they indicate about the type of file: Though some file formats may be indicated as being platform-specific in the chart, you will probably be able to view them in either with the appropriate software.
If you expected to receive music or an application and received a collection format instead, there is no need to be alarmed just yet: upon extracting the files from the collection with a program like 7zip or WinRAR, you can inspect the files within the collection to see if they seem legitimate. Look here for alternatives to 7zip and WinRAR for macOS.
In addition to comparing the type of your download to the file type you expect it to be, you should also stay informed about what kinds of software that you use has vulnerabilities. One notable example is the Microsoft Office suite, which can be exploited to take control of your computer if you attempt to open a malicious MS Word, PowerPoint, or Excel file.
Concerns about Malware
If you’re concerned about a website covertly installing malware on your computer, you can try scanning your computer for viruses with a malware scanner of your choice. Many antivirus programs cost money, and a good list to consider is here, but there are also free options, especially if you are only interested in using anti-malware to scan your computer. Malwarebytes, AVG, and Avast have been met with good reception according to users on the internet.
Staying Informed
It is important to stay aware of the software you use that could be vulnerable, as well as which technology companies do not always respect the privacy of their users. A good way to keep informed about this is to occasionally check technology news sites such as The Register, Wired, and Ars Technica.
One of the most important steps to staying protected from malware is keeping your software updated. This means making sure your operating system and software (media players, game clients, PDF readers, productivity tools, etc.) are up-to-date. Be cautious, however, as some companies may put out experimental updates to their software. If the company provides "security updates" or something with a similar name, those are definitely important and probably safe to download. Many software will keep itself updated automatically.
Sources
- https://transparencyreport.google.com/https/overview?hl=en
- https://www.globalsign.com/en/ssl-information-center/what-is-an-ssl-certificate
- https://www.spamtitan.com/web-filtering/critical-security-vulnerabilities-in-browser-plugins-addressed/
- https://www.cisdem.com/resource/7-zip-alternatives-for-mac-to-open-7z-files.html
- https://www.pcmag.com/picks/the-best-malware-removal-and-protection-software
- https://www.malwarebytes.com/?AVGAFFILIATE=3305&__c=1
- https://www.avg.com/en-us/homepage#pc
- https://www.avast.com/en-us/index?utm_medium=affiliate&utm_source=commissionjunction&utm_campaign=2190813&utm_content=13637464&couponfield=yes&cjevent=0b9fe072908311ea836600d80a24060b#mac
- https://www.theregister.co.uk/
- https://www.wired.com/
- https://arstechnica.com/
- https://www.spamlaws.com/identify-trojan-malware.html
- https://www.safetydetectives.com/blog/malware-statistics/
- https://usa.kaspersky.com/resource-center/threats/computer-viruses-and-malware-facts-and-faqs
- https://www.makeuseof.com/tag/websites-likely-infect-malware/
- https://www.bu.edu/tech/support/information-security/security-for-everyone/how-to-identify-and-protect-yourself-from-an-unsafe-website/