Virtual Private Networks

10 min read
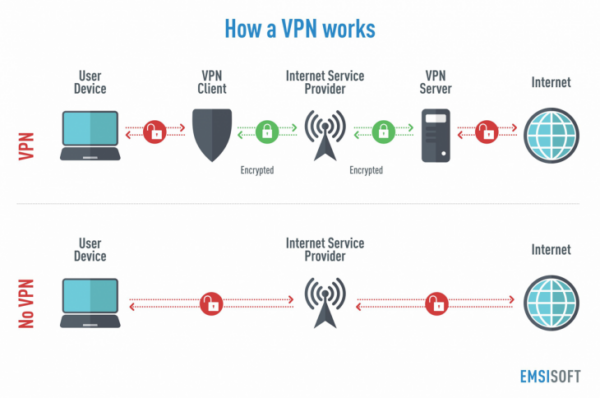
What is a VPN
VPN stands for Virtual Private Network. Traffic on this network is securely encrypted, thus this traffic/data remains private through its journey. This means that the data is unreadable to the likes of hackers and such.
Types of VPNs and Examples
There are two main types of VPNs that are used in practical settings: site-to-site and remote access.
According to Cisco, remote access VPN "securely connects a device outside the corporate office." For example, in office settings, remote access VPN allows people to, well, work remotely. That means that they can access a company's data and resources while it remains secure, even if the employee uses public wifi. Another example of remote access VPN that most of us have seen is UMD's DUO access system—think about it! ELMS is like our corporate office, and DUO protects that information, so that even when we access it on a public wifi (easily accessible by hackers), our information remains secure.
Cisco says that site-to-site VPN "connects the corporate office to branch offices over the Internet." For example, in office settings, this means that simply through the use of a router with an active user connection profile, "mini offices" can be set up outside of the main headquarters, which allow them to access the information of the HQ network, securely. This would be like a clothing shop setting up a mini pop-up shop in a mall, but still needing access to the company's database.
Understanding VPN
Understanding VPN requires an understanding of IP Addresses. An IP Address is a number that is assigned to each and every computer that in some way, shape, or form accesses the internet. It's called an IP address because it acts as just that—an address. If someone knows the IP address of your computer, they can find out where you're located, block you from visiting their sites based on certain locations, and hackers can even take over your computer just through your IPA. This is exactly what VPN works against. It temporarily "changes" your IP address, or masks it, so that the server thinks that your IP address is somewhere else (though not actually possible). Combined with data encryption/encapsulation, VPNs can boost security and reduce cyber crime, if used in the right way.
Privacy
In a non-corporate sense, a VPN can be used for privacy reasons. Even if you're just a regular person browsing the web, a hacker can use your IP address and find your entire browsing history based at that address. Of course, this is not ideal, especially if you have things like bank statements, bills, etc. This is where you might want to use a VPN and temporarily mask your IP address, as to not be the victim of fraud. For example, if you pay off a credit card bill in a coffee shop on their public wifi, this is EXACTLY what cybercriminals are looking for. Without a secure VPN, they will be able to access your data (though your bank is probably smart and uses a secure VPN already).
Benefits and Limitations
Advantages
- In terms of businesses, employees can use their local internet provider instead of using the 1-800- numbers. This leads to cost efficiency when connecting users to the employees' network
- VPN provides strong security utilizing "encryption and authentication protocols" (Henmi, Anne, et al.)
- VPN can increase flexibility and efficiency. VPN allows any mobile employees to have access to the companies high-speed internet connections.
- VPN increases protection for the average consumer. Public internet access that is used in public areas such as restaurants and airports can be a dangerous place for people. This is known to be a hot spot for hackers because the Wifi that these people are using is not secured by suitable encryption. This would allow hackers to easily steal viable data such as credit card information, passwords, and more. Connecting to a Virtual Private Network would apply that encryption to prevent hackers from being able to monitor your personal information whenever you are using WiFi for your devices.
Disadvantages
- VPNs are not always reliable. There is no major guarantee that the network will actually follow through with the quality of service. Similar to buying a new product that has no reviews. There are not many ways of determining if the VPN brand that someone will use will be completely optimal before purchasing the network. The only way to ensure the quality of service from the company is by purchasing the network. In many instances, there is a chance that one could save money in the long-run by avoiding hackers or lose money because they paid for the network and the system failed to secure private information.
- If VPN is not encompassed with a firewall it becomes vulnerable. The network has the ability to decrypt any traffic but does not have the ability to control traffic. This would lead to the company initiating a firewall behind the VPN which would force the user to continuously provide authenticity. This entails a depreciation of speed and efficiency within the VPN.
- In comparison to not utilizing a Virtual Private Network, using the network does lead to an increase in response time and memory usage, however, the difference in numbers are minuscule. A study to analyze VPN performance in Health Facilities identified that when the facility did not use VPN the response time is 0.0082 seconds and the memory usage is 14,543.6KB. When using the VPN the response time is 0.0714sec and the memory usage is 15,137.6KB. (Betuel, Siphael, et al.)
Plausible solutions to the limitations
The use of an Integrated VPN/Firewall would increase performance outcomes because the network would focus on decreasing congestion or networking issues. This would also increase the strength and reliability of the system to hold threats to a minimum.
- The Integration system would "prioritizing business-critical traffic over discretionary traffic to optimize available WAN (wide area networks) links" (Communication News).
- The system uses cryptographic acceleration cards to deposit any cyptographic operations on the host CPU onto a specific processor on the card.
- Other options are placing the firewall on the side or parallel to the VPN. However, these other techniques lead to a fall in speed, performance, and/or effectiveness of the network.
VPNs Cybercrime Prevention Strategies
Cybersecurity has become a significant issue in the past decade, as more and more of our personal information is accessible on the internet. In the past, most viruses were designed to just damage your computer as hackers had few ways to take advantage of the viruses. Nowadays, while accessing your device means being able to view your bank accounts, social security numbers and very personal documents, hackers want to enter your device without being noticed, copy everything you have, and use those data for their own dishonest ends.
There are so many ways to hack or gain access to a device, that it's best to have a secured server between you and any entity that wants your money or your life. The only difference between the thieves who claims money or threatens your life and the hackers, is that these days you won't even hear a question and they will probably take both your money and identity. Your bank details contain more than enough to steal your money and identity. With VPNs, instead of your personal firewall, you will be protected by huge servers with multiple security protocols, but to do so, You will need to select the best VPN available in order to take full advantage of it and browse securely.
Trusted VPNs increase the security of your online connectivity, transmitted data, financial transactions, and personal information, no matter where you are. They work by using a tunneling protocol that encrypts packet contents and wraps them in an unencrypted packet.
Important features of a secured VPN
- Encryption - converting information into a code to prevent unauthorized access
- Strict zero logging policy
- Servers (protocols)
Protocols used by VPNs
- Internet Protocol Security or IPSec
- Layer 2 Tunneling Protocol (L2TP)
- Point – to – Point Tunneling Protocol (PPTP)
- Secure Sockets Layer (SSL) and Transport Layer Security (TLS)
- OpenVPN
- Secure Shell (SSH)
Some trusted VPNs to use

If you don't use a VPN service to protect your online privacy, you're certainly at greater risk of cybercrime. The VPN service ensures that you can achieve maximum privacy, even with the simplest configuration.
Example cases
Case 1
In 2013, a family in Texas experienced an unusual baby monitor hack. A voice screamed through the monitor for the child to wake up and the voice also insulted the parents. The monitor relied on internet connection and using a VPN would have decreased the risk for this type of hack.
Case 2
A man named Sherjeel saw the direct effects of not using a VPN. So much so, that he recommends that everyone use a reliable VPN when accessing public WiFi at all times. According to Sherjeel, hackers lured him to a fake page where he ended up logging into two of his credit card accounts. Later, purchases from all over the world started to come in on his credit card. Sherjeel noted that he was nervous and frustrated throughout the process. This story shows the importance of using a VPN because, without one, you are more likely to be a victim of cybercrime.
Case 3
Sometimes, an ethical hacker can show just how risky public Wi-Fi can be. Maurits Martijn, a Dutch journalist at De Correspondent, was an ethical hacker that hacked a Starbucks. From his laptop within the shop, he was able to see a lot of data about what people were doing on their devices. For example, he could see the apps they had, the games they were playing, and shockingly—even passwords to sensitive information. Martijn shows us that it is not even that difficult for a hacker to get access to all of this information: the equipment to hack can be easily under a hundred dollars and the hacking itself took minutes. The lesson to learn from this is cybercrime is very easy to pull off. VPNs can prevent a person from becoming a victim.
Sources
What is a VPN
- "The Internet Isn't Safe. That's Why You Need a VPN." What Is My IP Address, whatismyipaddress.com/ vpn. Accessed 6 May 2020.
- "What Is a VPN? - Virtual Private Network." Cisco, www.cisco.com/c/en/us/products/security/vpn-endpoint-security-clients/what-is-vpn.html.
- "Remote Access VPN: Give Your Employees the Access They Need." Open VPN, openvpn.net/for/remote-access/.
- "Scale Your Business to New Locations Securely with Site-To-Site VPN." Open VPN, openvpn.net/for/site-to-site-vpn/.
Benefits and Limitations
- Betuel, Siphael, et al. "An Experiment to Analyze Performance of Virtual Private Network Approach to Information Exchange between Health Facilities." Applied Medical Informatics, vol. 39, no. 1/2, Mar. 2017, pp. 21–29. EBSCOhost, search.ebscohost.com/login.aspx?direct=true&db=asn&AN=128867904&site=ehost-live.
- Henmi, Anne, et al. Firewall Policies and VPN Configurations. Syngress, 2006. EBSCOhost, search.ebscohost.com/login.aspx?direct=true&db=nlebk&AN=170636&site=ehost-live.
- Panova, Evgeniya, and Gareth Stephens. "Three VPN Use Cases You Should Know About." Dataconomy, 25 Feb. 2020, dataconomy.com/2020/02/three-vpn-use-cases-you-should-know-about/.
- "Three Crucial Elements for Maximum Security." Communications News, vol. 38, no. 12, Dec. 2001, p. 38. EBSCOhost, search.ebscohost.com/login.aspx?direct=true&db=asn&AN=5699149&site=ehost-live.
- how-a-vpn-works-infographic-730x484_orig
VPN Cybercrime prevention strategies
- Sahu, Pawan. "How To Strengthen Web Security with VPN." United States Cybersecurity Magazine, 26 Oct. 2018, www.uscybersecurity.net/vpn/.
- Poremba, Sue Marquette. "How a VPN Can Boost Your Security and Privacy." Tom's Guide, Tom's Guide, 29 Oct. 2018, www.tomsguide.com/us/-vpn-for-beginners,news-17514.html.
- Marshall, Adam. "The Best VPN Service 2020." TechRadar, TechRadar, 4 May 2020, www.techradar.com/vpn/best-vpn.
Example Cases
- Team, Strong. "True Cybercrime Horror Stories." StrongVPNcom Blog, 23 Oct. 2018, blog.strongvpn.com/true-cybercrime-horror-stories/.
- "The 12+ Internet Crime Stories That Make Cybersecurity Measures Essential." N.p., 27 Jan. 2020. Web. 07 May 2020.
- "True Cybercrime Stories. Real People, Real Losses." NordVPN, 3 Mar. 2020, nordvpn.com/cybercrimes/sherjeel/.