White Hat Hackers

5 min read
What are White Hat Hackers
White Hat Hackers are considered to be ethical hackers. They use their software hacking knowledge to improve holes in security. These hackers are often paid employees or contractors of companies and government agencies. They perform vulnerability assessments, test security systems, and perform penetration testing.
The Importance of Ethical Hacking
New viruses, malware, worms, and ransomware are spreading through the internet and to our computers every day. With the total amount of malware infections rising from 12.4 million in 2009 to 812.67 million in 2018, there is an urgent need for ethical hacking services to protect government agencies and businesses. White hat hackers have an important role in fixing issues in software that can lead to attacks.
Ethical hacking is used as a way to analyze the security systems and programs of an organization. The main goal of ethical hacking is to prevent important data from being stolen and used maliciously. But there are other benefits from ethical hacking: discovering vulnerabilities in software that an attacker can manipulate, protecting data from terrorists, and preventing breaches in security by implementing a secure network. Overall, there is a need for ethical hacking as security threats have multiplied and it is necessary to take preventive action against hackers.
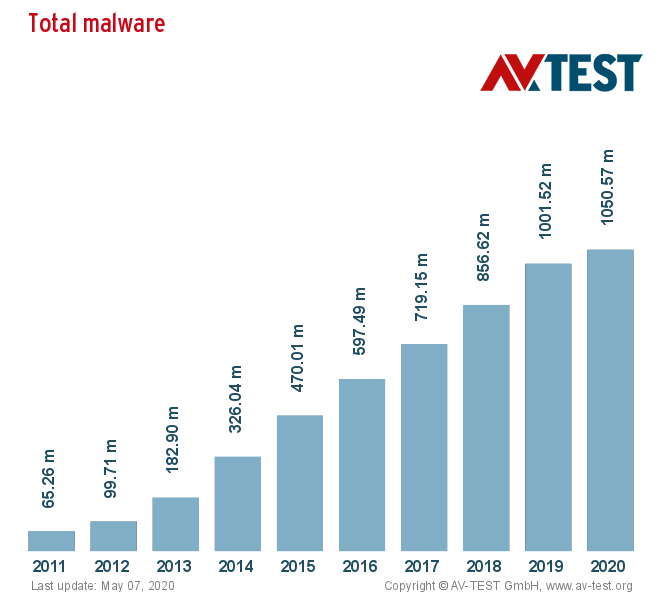
The amount of malware has drastically risen in the past decade:
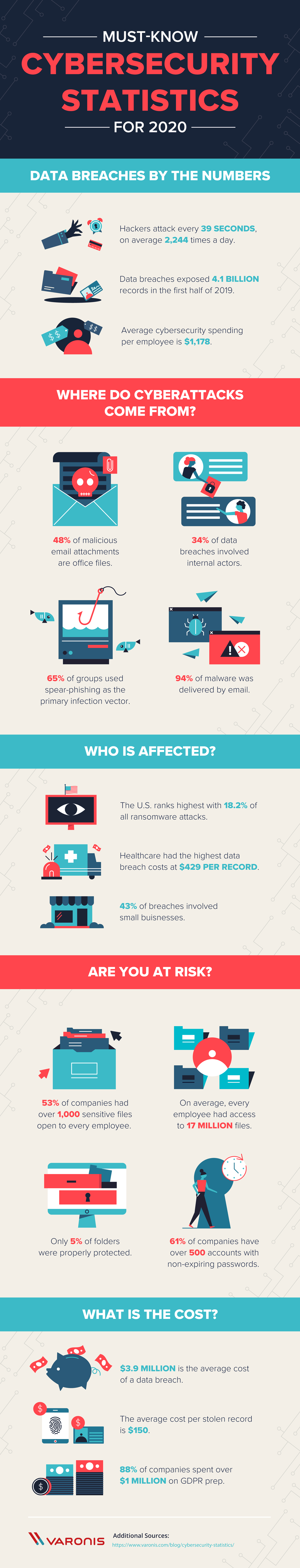
Bug Bounties
Ethical hacking does not only come in the form of random acts of kindness. White hat hackers can be contracted to test the systems of the hiring entity. Another way they can be compensated for their work is through bug bounties. Bug bounties are rewards offered by organizations to whoever can discover exploits in their system. These rewards can range quite drastically depending on how serious the uncovered problem is. Google for example has paid out more than $15 million since 2010. The Federal Government has also taken interest in this as in 2016, the Department of Defense launched its Hack the Pentagon program in conjunction with HackerOne. This event served as a stepping stone for other bug bounty events involving the Federal Government which plays a vital part in strengthening national security. This method gives an incentive to white hat hackers to make entities aware of threats before black hat hackers can abuse them. Considering how much damage can be avoided, bug bounties are a cheap way to patch dangerous vulnerabilities. They also serve an important role in supporting more people to become white hat hackers as there are potential career opportunities. To get a better understanding of how big bug bounties are becoming, here is a comprehensive list of current bounties: https://www.bugcrowd.com/bug-bounty-list.
Advice from a White Hat Hacker
The job of a white hat hacker is to try and hack a person or organization to see if they are vulnerable to attacks by malicious hackers. If they find a weakness in their client’s security, the white hat hacker will advise them on how to strengthen that aspect of their security. White hat hackers have an expert understanding of how a client’s security can be compromised which means they can offer expert advice on how to stay secure. In an interview with Mike Elgan from computerworld.com, famous hacker Kevin Mitnick gives his advice on how you can secure your smartphones and computers.
Kevin Mitnick is one of the world's most famous hackers. According to his website, mitnicksecurity.com, he hacked into at least 40 major corporations just to challenge himself. His hacking earned him a spot on the FBI’s most-wanted list and he was on the run for three years until he was captured. When he got out of jail, he decided to use his knowledge for good and now he is the CEO of Mitnick Security Consulting.
Almost everyone today owns a smartphone, so it is important for people to know how to secure it. One of the basic tips Mitnick gives is to use a longer password. Many smartphones have a default password length of only a couple of characters. The iPhone, for example, has a default password length of 4 characters. Smartphone users should use a longer password if they want their phones to be more secure. You should use longer passwords for all devices and accounts because the longer your password is the harder it is to crack.
Laptops and desktops are owned by many and are also vulnerable to being hacked just like smartphones. To keep these devices secure Mitnick advises installing anti-virus software and taking advantage of security features offered by your computer. One example of a helpful security feature is how Apple gives you the option to only be able to download Apple-approved apps. The other option allows you to download Apple-approved apps and apps from identified developers. Mitnick does not like this option because it does not take much to become an identified developer.
Sources
- https://www.eccouncil.org/ethical-hacking/
- https://purplesec.us/resources/cyber-security-statistics/
- https://www.mitnicksecurity.com/about-kevin-mitnick-mitnick-security
- https://www.computerworld.com/article/3041073/surprising-tips-from-a-super-hacker.html
- https://www.pcmag.com/news/7-huge-bug-bounty-payouts
- https://ma.hacker.one/rs/168-NAU-732/images/hacker-powered-security-report-2017.pdf
- https://www.hackerone.com/hack-the-pentagon
- https://www.av-test.org/en/statistics/malware/
- http://yournetflixspremiumaccount.blogspot.com/2018/04/white-hat-hackers.html
- https://www.varonis.com/blog/cybersecurity-statistics/